You can think of proxies like a middle man. It works by sitting between you and website that you are trying to visit. Enterprises might use this to monitor their employee’s web usage, people may use this to prevent websites from learning about your location, and hackers use this to intercept requests made from an application to certain endpoints (we actually use them for much more than this). During mobile application security testing, one of the greatest hurdles is being suitably positioned between the application and its APIs or endpoints its talking to. This post will address how to intercept requests made with applications that doesn’t respect system level proxies.
Android
There are potentially three probable cases why after installing a CA certificate in the system trust level, and configuring proxy settings on the wireless interface traffic from the application still doesn’t appear in your proxy application.
- The android application is setting another proxy in its http requests, and will thus ignore system level proxies.
- The android application is setting http handlers to ignore system level proxies which will connect directly to the endpoint it is communicating with.
- The android application is not using http(s) protocols.
Host File Changes
This is possible if you have read-write privileges on the system directory. Usually, this is already enabled given that the Android device was jailbroken successfully. Use wireshark to find out what domains it is reaching out to, this should be trivial (look at the DNS packets).
In your /etc/hosts file, append the following lines. Assuming 192.168.1.20 is your proxy server.
192.168.1.20 mobile-endpoint.com
192.168.1.20 uend-authentication.com
Burpsuite Proxy Settings
Your proxy settings for Burpsuite should look like the image below. Other proxy software should also capable of doing this.
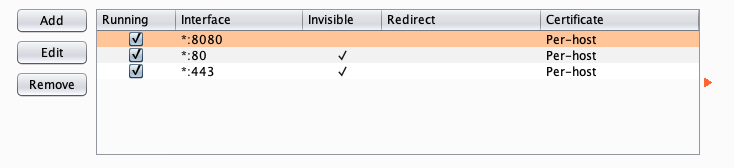
By taking control of the local DNS, it is possible to force the application’s endpoints to our proxy address. The only caveat for this is that if the application is communicating to the host via IP addresses, this technique will fail. However, that occurence is rather rare.
iPhone - iOS
Using the same technique above may not work in most cases. Though, one should take this with a grain of salt since only testing was done on iOS 11 to iOS 12. In a certain Apple developer forum, one Apple staff shed some insight that led me to conclude that most applications will in fact ignore the /etc/hosts or /private/etc/hosts file even though it exists (the browsers respect it to a certain extent). Below is a small list of problems with other software.
-
Charles Proxy: This is a commercial tool. Also, its DNS Spoofing doesn’t seem to intercept all requests, and may miss endpoints of interest.
-
Wireshark: It’s actually possible to make an additional network interface to directly capture packets from the iOS device. This method is excellent if the calls aren’t encrypted. But you won’t be able to do much if they are.
-
PPTP: Since iOS 10, support for PPTP VPN has been dropped.
Tunnelling Traffic through Openvpn
Spin up a local Kali or Ubuntu vm, and go through the prompts from the following script:
Configure iptables to redirect all traffic going to ports 80 and 443 to 8080.
iptables -t nat -A PREROUTING -i tun0 -p tcp --dport 80 -j REDIRECT --to-port 8080
iptables -t nat -A PREROUTING -i tun0 -p tcp --dport 443 -j REDIRECT --to-port 8080
Burpsuite Proxy Settings
Note that the image below has invisible proxy set in the request handling tab. This is necessary because the resulting requests will not be in the form that is normally expected by an HTTP proxy.
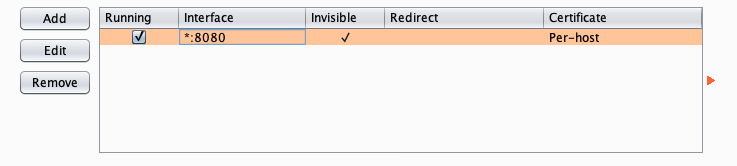
Conclusion
Just a post to consolidate endless hours of googling. Hopefully this saves someone trouble when performing security testing on mobile applications. Ciao.